Recently, investigative reporter Yehuda Miller got a number of FOIA files that totally redefine what we were informed to think about the 2020 United States governmental election.
The election was billed by the Democrat Party, Joe Biden, the mainstream media, and previous CISA Chief Chris Krebs as the most safe election in United States history.
Chris Krebs, the previous CISA Director fired by Donald Trump, affirmed before Congress on December 16, 2002, after he was fired. Krebs was contacted us to affirm before the United States Senate Homeland Security Governmental Affairs Committee.
Krebs notoriously revealed that day, “The 2020 election was the most safe in United States history.”
But was 2020 actually the most safe election in United States history?
Yehuda Miller and The Gateway Pundit strategy to launch a series of FOIA files in the coming days that show Chris Krebs was not sincere with the American public throughout his statement which he plainly understood his declarations were unreliable.
On Monday, we launched info on a trick 2020 Election Day telephone call arranged by The Cybersecurity and Infrastructure Security Agency (CISA)
CISA explains itself as the functional lead for federal cybersecurity and the nationwide planner for important facilities security and durability. Considering that its starting, CISA has actually changed into a much more ominous and politicized company.
Founded in 2018, CISA was initially planned to be a supplementary company developed to secure “vital facilities” and defend against cybersecurity risks. In the years given that its production, nevertheless, CISA metastasized into the switchboard of the federal government’s domestic security and censorship operations on social networks.
By 2020, CISA regularly reported social networks posts that apparently spread out “disinformation” to social networks platforms. By 2021, CISA had an official “Mis-, Dis-, and Mal-information” (MDM) group. In 2022 and 2023, in reaction to growing public and personal criticism of CISA’s unconstitutional habits, CISA tried to camouflage its activities, duplicitously declaring it serves a simply “informative” function.”
The Gateway Pundit’s Jim Hoft is presently the lead complainant in the Missouri-Louisiana vs. Joe Biden claim that is heading to the Supreme Court in March.
The complainants are challenging the Biden program’s censorship device, arguing that the federal government can not infringe on the complimentary speech of Americans. CISA today is main to the federal government’s censorship system.
On Monday, The Gateway Pundit launched proof that a personal conference was arranged by CISA authorities on November 3, 2020, at 3: 30 PM Eastern Time with choose members of a secret “Election Security Initiative.”
This was an unique conference of CISA authorities and their unique election Partners. This was held late in the afternoon on Election Day. It supposedly lasted for a half hour.
The Gateway Pundit released this report on Monday.
You can checked out the very first report here and listed below:
Today, The Gateway Pundit is launching brand-new info that shows Chris Krebs was not truthful throughout his statement in December 2020.
Yehuda published this letter to America last night on X:
Dear America,
You have actually been informed by CISA the 2020 election was “Safe and Secure”.
Yet CISA, made a report on the security and vulnerabilities of lots of “Election Infrastructure” (EI) workplaces throughout the nation for the 2020 election year.
The report was concealed from the general public.
The report has actually now been lawfully gotten through Freedom of Information Act FOIA.
You do not require to be a computer system guy to comprehend from it that our election workplaces have to do with as permeable as Swiss cheese.
It appears to be the best 14 th change infraction, by dealing with citizens in a different way. All citizens need to have the ability to enact the very same safe and secure style.
Read the report with your own eyes and ask yourself why this was concealed from the general public?
Do you still rely on any authorities who understood about this yet stopped working to inform the general public?
Yehuda Miller just recently acquired the Election Infrastructure (EI) Subsector Cyber Risk Summary report for 2020 through a FOIA demand.

The report supplies analysis, findings, and suggestions originated from non-attributable cybersecurity patterns observed in between November 3, 2019, and November 3, 2020— Election Year 2020 (EY20).
The report was released in March 2021 and consisted of the information understood to the CISA authorities for Election Year 2020.
On page 2 of the report– CISA released its analysis of the United States Election Infrastructure (EI) entities in 2020.
CISA’s analysis of the offered information for examined EI entities discovered:
76% of EI entities for which CISA carried out a Risk and Vulnerability Assessment (RVA) had spearphishing weak points, which offer an entry point for foes to introduce attacks
48% of entities had a crucial or high intensity vulnerability on a minimum of one web available host supplying prospective attack vectors to foes
39% of entities performed at least one dangerous service on an internet-accessible host, offering the
chance for hazard stars to assault otherwise genuine services34% of entities ran unsupported os (OSs) on a minimum of one web available host, which exposes entities to jeopardize.
From page 2 of the report– the highlights are our own:

How can 2020 be thought about a “protected” election when 76% of Election Infrastructure had spearfishing weak points, and 48% of the entities had an important or high vulnerability on a minimum of one internet-accessible host?
The CISA report then continues to explain how election authorities can remedy these vulnerabilities in the system. Certainly, this indicates the vulnerabilities are still available to foreign stars.
On page 4 of the report– CISA reports that an Advanced Persistent Threat (APT) effectively acquired United States citizen registration information!
In the run-up to the 2020 election, an APT star effectively acquired U.S. citizen registration information, consisting of in a minimum of one circumstances from a state election site, and released an election-related disinformation project. In October 2020, CISA likewise observed APTs targeting elections facilities in state, regional, tribal, and territorial (SLTT) federal government entities’ networks. Since October 24, 2020, CISA had no proof to suggest that stability of elections information was jeopardized.
On page 7 of the report— CISA CyHy scanning discovered 48,796 overall vulnerabilities on hosts in the 324 getting involved EI entities.
Of those vulnerabilities, 319(0.80 percent) were of important seriousness, and 1,820(4.55 percent) were of high intensity based upon the CVSS base rating.
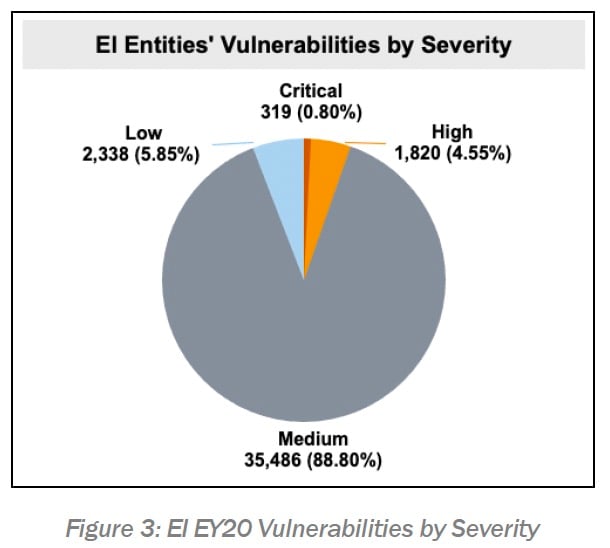
On page fifteen of the report— Officials discovered another 451 vulnerabilities and weak points in the systems.
In EY20, CISA carried out RPTs and RVAs for 108 EI entities. RPT and RVA groups carried out penetration tests, phishing evaluations, web application evaluations, and database evaluations. These groups determined 451 findings (see figure 12), which are vulnerabilities and weak points that provide a threat to the entity.
Does that sound safe and secure to you?
How can anybody declare the 2020 election was “the most safe and secure election ever” when his company’s own reporting states 76% of the facilities had spearphishing weak points, 48% of the facilities had vital or high intensity vulnerability, and 39% of the facilities performed at least one dangerous service on an internet-accessible host?
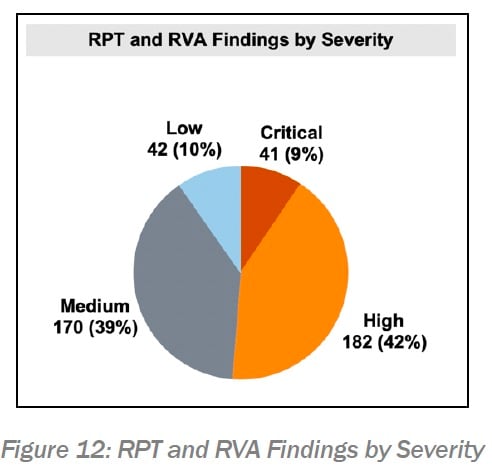
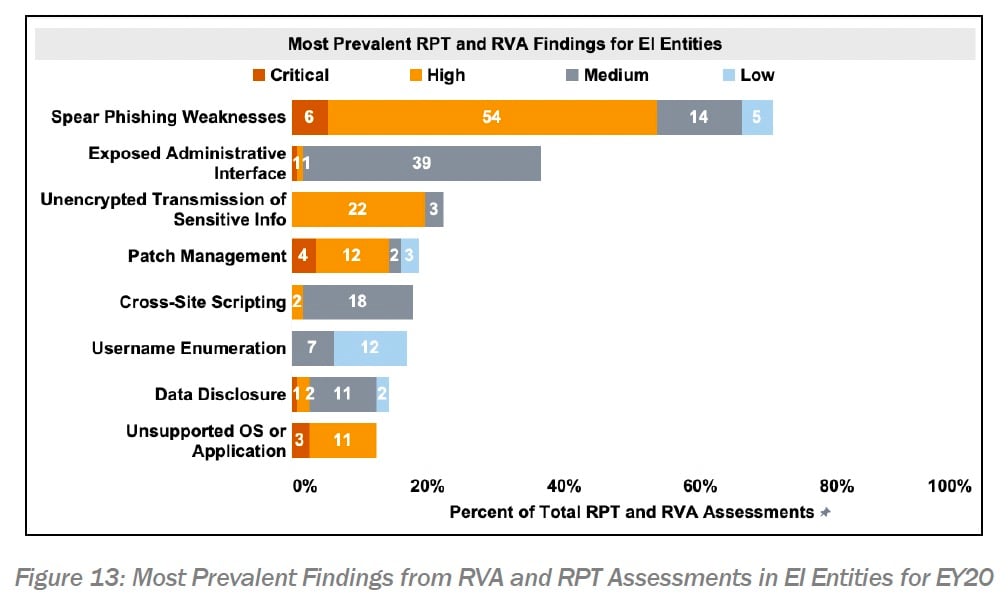
On pages fifteen and sixteen of the report — More is talked about on the spearphishing hazards.
During the evaluations, spearphishing weak points were the most typical finding observed in 73 percent of entities (see figure 13). The broad success of spearphishing shows that examined entities had insufficient border and host-level defenses. This weak point enabled spearphishing e-mails to go through the network border and consequently perform on the regional host with the help of a user carrying out some action, like clicking a link or opening a file that starts the execution of destructive payloads. In addition to suggesting an absence– or bad application– of technological defenses, this finding can likewise suggest an absence of cybersecurity awareness and acknowledgment of spearphishing by users, which leaves the entity susceptible. This finding is considerable for all EI entities to examine and attend to, as numerous danger stars frequently start attacks by using spearphishing to record qualifications and develop preliminary remote gain access to.
This report by CISA totally damages previous DHS authorities Chris Krebs and his outrageous testament under oath before the United States Senate.
Obviously, Krebs was not sincere with the Senate Committee in 2020.
The Gateway Pundit and Yehuda Miller intend on launching more incriminating files in the days ahead.
Here is the complete CISA Election Infrastructure Subsector Cyber Risk Summary report on 2020 vulnerabilities.
The post EXCLUSIVE: Former CISA Chief Chris Krebs LIED Under Oath When He Said 2020 Was Most Secure Election Ever– Now We Have the PROOF! And Krebs remains in BIG Trouble! appeared initially on The Gateway Pundit





This article may have been paraphrased or summarized for brevity. The original article may be accessed here: Read Source Article.





![President Trump Gives Barron A Shout Out At Inaugural Parade: His Unexpected Response is Pure Gold! [VIDEO] president-trump-gives-barron-a-shout-out-at-inaugural-parade:-his-unexpected-response-is-pure-gold!-[video]](https://news.lateawakening.com/wp-content/uploads/2025/01/35545-president-trump-gives-barron-a-shout-out-at-inaugural-parade-his-unexpected-response-is-pure-gold-video-100x70.jpg)



